What are the security benefits of thin clients and zero clients ?

Courtesy of the internet, the amount of knowledge a person can acquire now has no bounds. As a result of this, a regular office employee is now more “tech savvy” than before. This in return has brought a challenge known as “Shadow IT” to the IT department. Shadow IT is a phenomenon which represents use of different applications or services by a user to make his/her work easier. However, these applications or services are not approved by the IT department, hence can pose a severe security threat to the enterprise data.
One of the best ways to mitigate this risk is to make the endpoint or the user device more secure and controlled. However, with a traditional PC or laptop, this can be a challenge as well for the IT department. This where a thin/zero client comes to the rescue.
How do thin and zero clients improve overall security?
Thin clients are inherently restricted and are managed by a server. The end users use virtual applications and desktops to get their work done. As a result of this architecture, all the sensitive data is now on a central server hence preventing any malicious access to it. Also, due to central management, it is very easy for the IT department to push security upgrades to all the endpoints together.
What type of data security do thin and zero clients offer?
The feature that provides the biggest security advantage to a thin/zero client is that it has a read only file system. As a result of this, end users cannot download any non-approved applications or copy any malicious data on the endpoint device. The other feature that makes thin/zero client secure is that there is no local user data storage on the endpoint device. All the user data is stored on the central server and the endpoint accesses the data from there. This greatly reduces the risk of data loss or theft from the endpoint device.
Due to both of these features, thin/zero clients have a zero-attack surface. Meaning there is nothing on the endpoint device for a hacker to attack. There is no data to steal neither any application with sensitive data to attack with malware.
While a thin/zero client comes with all these awesome features, a lot relies on the operating system on it as well. Also, as a thin client has limited local capabilities, most of them come with a management software that allows you to manage these devices. The security features of the operating system and management software also play an important role in the overall security of the solution.
ZeeTerm, a thin client solution by ZeeTim
ZeeTerm ticks all the above features and comes with the below security focused Linux based operating system and management software:
ZeeOS
It’s a state of the art customized Linux operating system developed by ZeeTim, that has been optimised for thin client devices. It provides a maximum level of security and network performance. It has been adapted for optimising the performance of different virtualization protocols such as Citrix ICA, Microsoft RDP, VMware Blast, etc.
ZeeConf
A device management tool that centralizes the configuration process of all of the deployed devices. It supports a multi-tenant mode, allowing you to manage different clients or departments using a role-based administration via ZeeConf client.
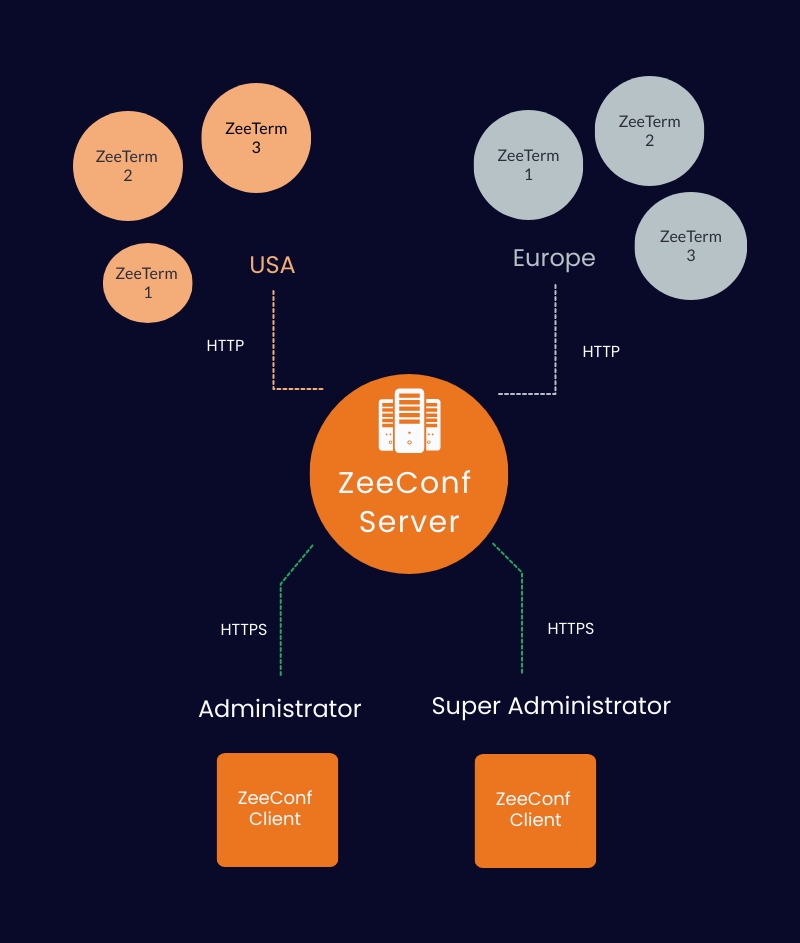
What type of security does ZeeOS provide?
As ZeeOS is a Linux based operating system, it reduces the risk of virus attacks to a great extent. It enforces complete separation between the installed packages which in return enhances the security and allows better management of applications. Being a read only OS, it offers complete protection from external programs and malware attacks. Apart from all of these, it is fully compliant with all of the standard security protocols.
How is the connection between ZeeConf and ZeeTerm secured?
In a client-server deployment, ZeeConf client connects to ZeeConf server only via HTTPS, providing a completely secured connection. Apart from this, ZeeConf clients can directly connect to ZeeTerm without the server via SSH. This SSH connection is secured via a pair of security certificates and keys which can only be known to the administrator. There’s no other way to connect to a ZeeTerm to modify anything on it. This architecture prevents a lot of network attacks such as “Bagle malware” and there’s no need for an anti-virus as well.
To know more, please get in touch with ZeeTim and we will be glad to take you through our endpoint solution for any type of virtualization infrastructure.
Tags In
Search
Recent posts
- ZeeScan is now available on the VMware Marketplace 22 April 2024
- The main Cybersecurity risks of remote work: Safeguarding your infrastructure in a connected world 3 April 2024
- Introducing the latest version of ZeeScan! 22 February 2024
- Chromebooks in Business: Advantages and Challenges to Consider 19 February 2024
- Happy New Year from all of us at ZeeTim! 1 January 2024




